By Bryan C. Peters
Despite the undeniable social relevance of piracy, criminologist have lagged behind other fields in its study. In 2009, Forsyth, Gisclair and Forsyth aptly noted that, “most criminologists are landlocked…as if crime on the water did not exist”.1
Although interest is slowly growing within the field, the potential utility of criminological theories and analytical tools have yet to be broadly exploited. One such tool is crime script analysis. With roots in rational choice theory and the cognitive sciences, crime script analysis was developed by criminologist Derek Cornish.2
A straightforward and pragmatic tool, crime scripts are “step-by-step accounts of the procedures adopted by offenders to successfully commit a particular crime”.3 Crime script analysis allows the researcher to systematically investigate the entire crime commission process, including actions taken before, during and after a crime has been committed.
Conducive to a variety of methodological and data collection strategies, crime script analysis has been applied to a number of crime types ranging in complexity from simple, low-level crimes such as shoplifting, pickpocketing and theft to more complex ones including corruption, cybercrimes and child sex trafficking (refer to Dehghanniri & Borrion, 2019 for more examples). More practically, crime scripts can be used by policy-makers and private entities to identify possible intervention points to disrupt the crime commission process. Further, crime scripting is a fluid process. As more and better data is collected, scripts can easily be revised and interventions can be reassessed and changed accordingly.
In a recent article published in the International Journal of Law, Crime and Justice, I employ crime script analysis to articulate detailed business models for each type of piracy in the waters within and off Nigeria. In this first application of crime script analysis to piracy, I show the utility of this technique in counter-piracy efforts and its potential application to other regional piracy manifestations, and to ‘blue crimes’ more broadly.4
Crime script analysis applied to Nigerian piracy
The Nigerian piracy manifestation was the obvious choice to test this analytical tool. As the epicentre of piracy in the Gulf of Guinea (GoG) and the contemporary global ‘hot spot,’ piratical acts perpetrated in these waters are particularly troubling and violent, with far reaching consequences.
Figure 1. Nigerian Piracy Incidents (2009 – 2018) (Source: Peters, 2020)
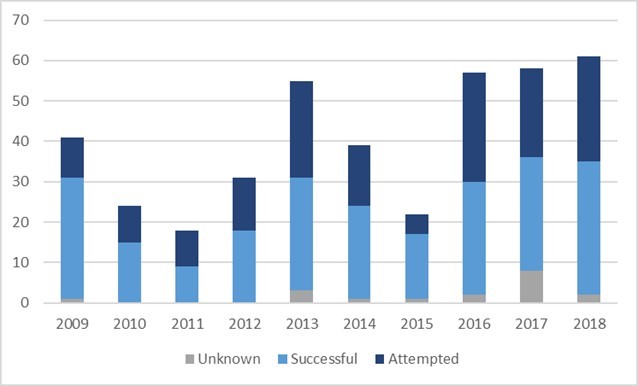
The analysis relied upon the comprehensive International Maritime Bureau (IMB) piracy definition: “An act of boarding or attempting to board any ship with the apparent intent to commit theft or any other crime and with the apparent intent or capability to use force in the furtherance of that act.” 5
To classify piracy incidents, I employed Justin Hastings’ offense-based typology which includes kidnappings for ransom, robberies and ship/cargo seizures. 6 I also chose to include attempted attacks (suspicious approaches and unsuccessful boardings) as they were quite common and had the potential to produce significant harms.
Combining publicly available incident report data from multiple sources (IMB, International Maritime Organization and the U.S. National Geospatial Intelligence Agency), I created a dataset containing 406 piracy incidents perpetrated between 2009 and 2018.7 Most incident reports provided structured data fields (e.g., incident date, time, vessel characteristics and geographic coordinates) as well as brief, unstructured incident summaries which also provided a wealth of information.
Since there was some overlap between data sources, care was taken to ensure that duplicate incidents were not recorded in the dataset. To compensate for the high rate of partial- and under-reporting, the primary data collection was supplemented with insights from piracy literature and interviews with piracy experts.
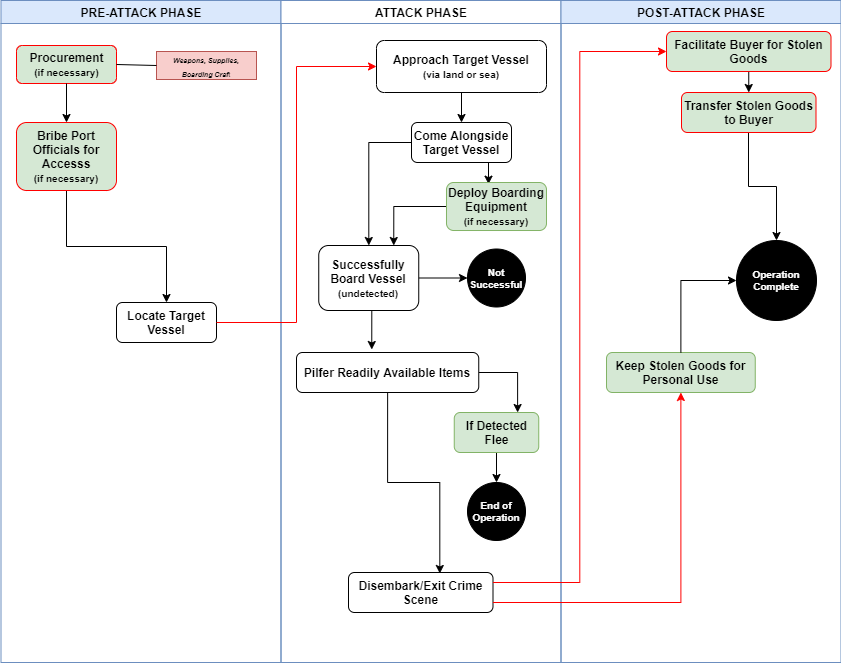
Using content, descriptive statistical and geospatial analysis, I was able to piece together detailed business models for each piracy type. The business models depict “the typical logistics or modus operandi of a criminal activity”8 and include perpetrator characteristics, resource requirements, operational phases, script activities, spatial distributions and accompanying and enabled criminal activities.9 Each business model was organized into three distinct operational phases: pre-attack, attack and post-attack. To highlight script activities and the sequence of events during an attack, crime script diagrams were created for each piracy-type.
It should be noted that these diagrams are meant to show only the “typical” crime commission process – incidents do not always follow the same progression nor do they always require the same resources and script activities. During the initial stages of the research, based on the level of organization and resource requirements, it became clear that two distinct sub-types of robberies were common in Nigeria, petty (mostly in port and anchorage areas) and organized (occurring further offshore by larger, more organized groups operating out of the Niger River Delta). As such, it was decided to construct separate scripts for each sub-type.
Figure 2. The Scripts (by piracy-type)(Source: Peters, 2020)
Diagrams show the “typical” crime commission process—some incidents do not require every script activity nor do they always follow the exact sequence of events. White text boxes signify activities that are common to most cases. Red text boxes depict common activities typically involving corruption. Green text boxes signify actions that occasionally occur (those outlined in red can involve corruption). Black circles signify the operation end-point and arrows indicate the transition between operational phases.
1. Kidnapping for Ransom
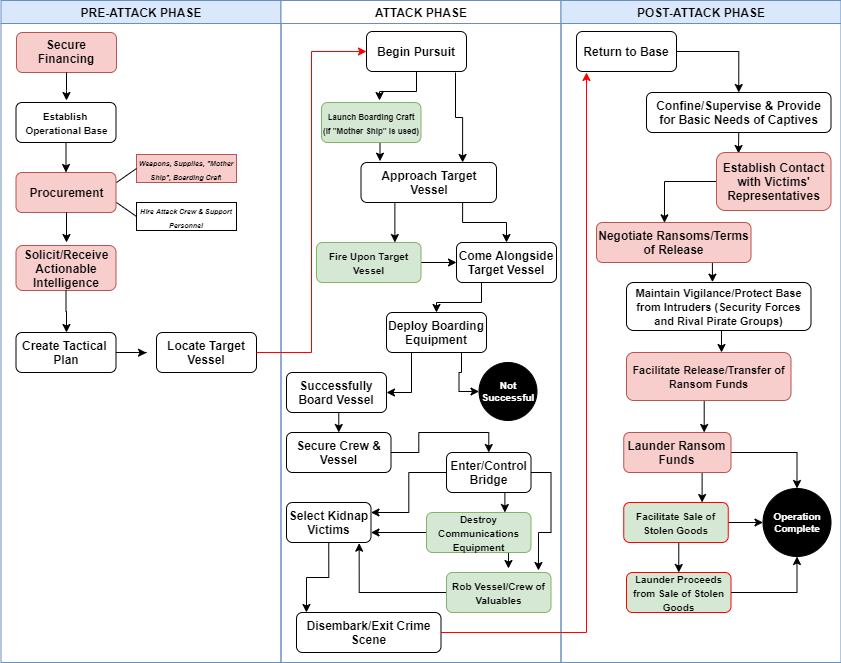
2. Cargo Seizure (Oil)
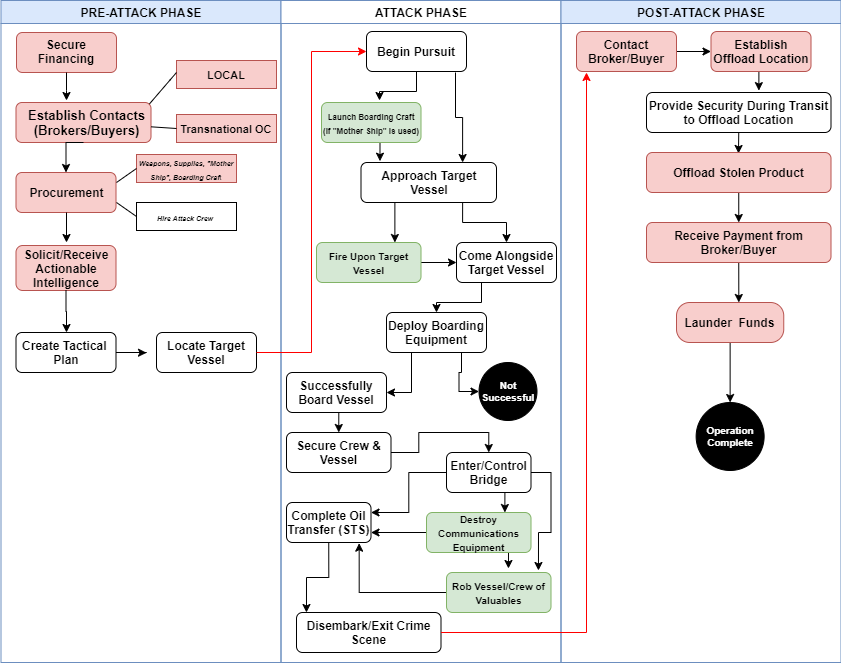
3. Robbery (Organized)
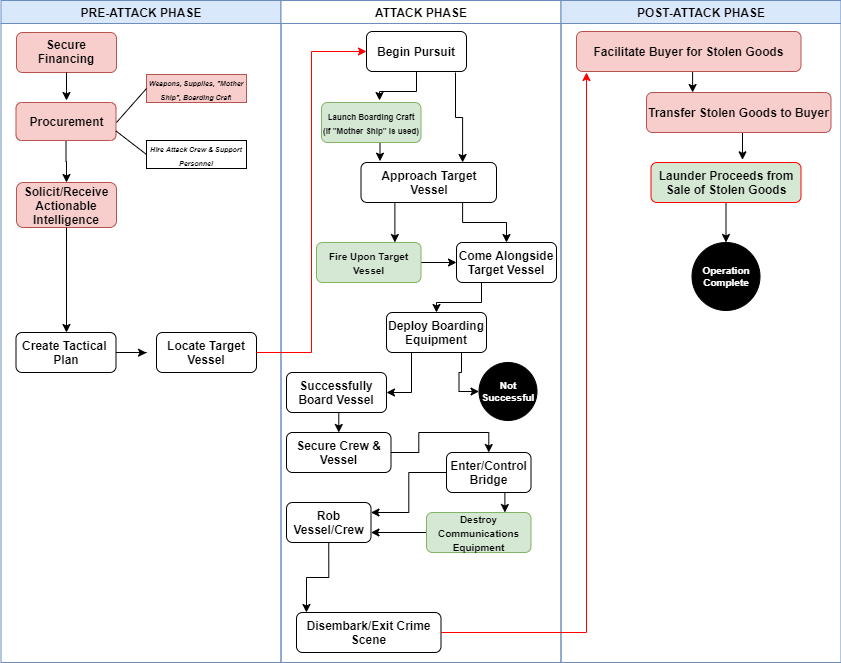
4. Robbery (Petty)
Research highlights and concluding remarks
There were two overarching goals of this research. The first was to highlight the utility of this analytical technique in studying piracy, and by extension, other ‘blue crimes.’ The second was to stimulate criminological research on piracy, and more broadly, to show the potential of applying criminological theories to the study of piracy. More practically, the piracy business models highlight the importance of investigating each piracy-type independently, allowing policy-makers to identify commonalities as well as the unique differences between them and to design custom interventions tailored for each.
Although crime scripting can be used in developing long-term counter-piracy interventions, due to the intensification and violent nature of the Nigerian manifestation, I chose to focus only on those that could be implemented in the short-term to protect those in immediate risk, seafarers and fishermen. I provide several examples of situational prevention and tactical enforcement measures that can be used by both public and private actors to protect those most vulnerable to attack. A few examples include:
- Employing proven ship-borne measures designed to increase pirates’ perceived risk and effort such as having a visible ant-piracy watch, increasing deck lighting and, when under attack, the use of evasive maneuvering, increasing speed and mustering crewmembers (for more examples see Shane et al., 2015 and Shane & Magnuson, 2016)
- Increasing vigilance during risky STS operations to reduce vulnerability
- Targeting pirate operational bases in the Niger River Delta since these groups are responsible for many of the most serious incidents
- Bolstering security in vulnerable port-areas with a focus on waterborne threats (this analysis revealed that most port incidents were perpetrated via the water and not from the land)
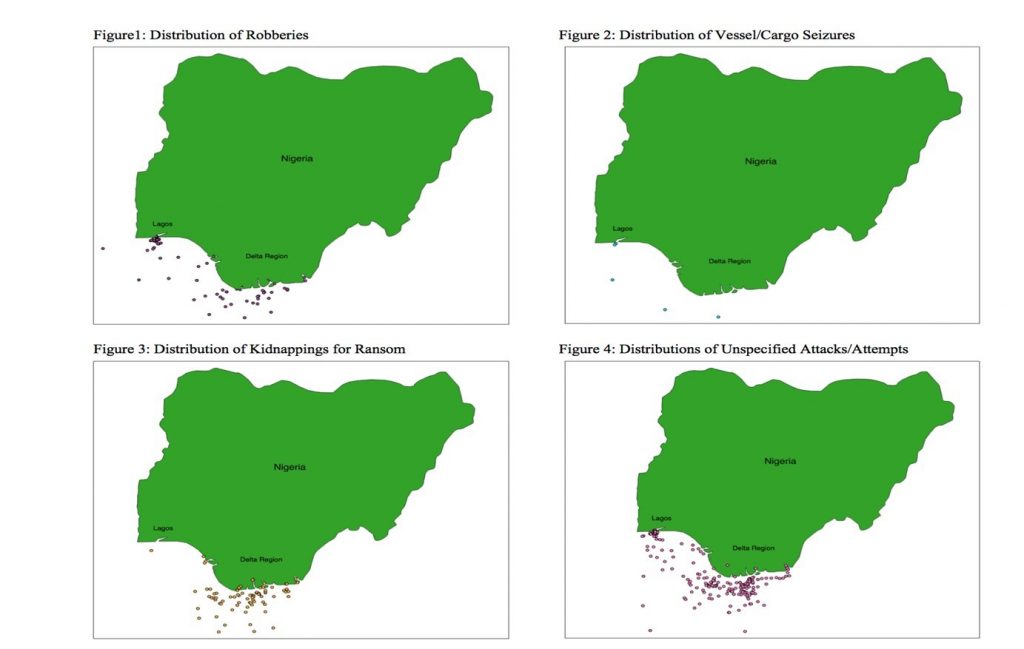
On a side note, the geospatial analysis also revealed distinct spatial patterns between piracy-types in Nigeria—information that can also be used in developing tactical interventions.
Figure 3. Spatial Distributions of Piracy Incidents by Type (2009 – 2018) (Source: Peters, 2020)
Looking to the future, crime scripting could be applied to other regional piracy manifestations and to a variety of other ‘blue crimes.’ Crime scripting can also be used in the process of assessing the harms of piracy and to ultimately develop harm reduction strategies. Greenfield and Paoli have developed a multi-step analytical framework to systematically assess the harms of crime and have applied it to a variety of complex crimes.10
The construction of business models using crime scripting is the first step within this framework. It is also the most important one since it serves as the building block for the others. In a forthcoming article in Acta Criminologica: African Journal of Criminology and Victimology, Dr. Letizia Paoli (KU Leuven) and I build upon this research and systematically assess the harms associated with the Nigerian piracy manifestation.
References and further reading
Cornish, Derek B. 1994. The procedural analysis of offending and its relevance for situational prevention, in Clarke, R.V. (Ed.), Crime Prevention Studies 3. Monsey: Criminal Justice Press.
Dehghanniri, Hashem and Borrion, Herve. 2019. Crime scripting: A systematic review. European Journal of Criminology, https://doi.org/10.1177/1477370819850943.
Forsyth, Craig J., Gisclair, Kay H. & Forsyth, York A. (2009). Waterborne crime: Examining contemporary piracy. Deviant Behavior, 30: 669-679, https://doi.org/10.1080/01639620902797655.
Greenfield, Victoria and Paoli, Letizia. (2013). A framework to assess the harms of crimes. British Journal of Criminology, 53: 864-885, https://doi.org/10.1093/bjc/azt018.
Hastings, Justin V. (2012). Understanding maritime piracy syndicate operations. Security Studies, 21(4): 683-721, https://doi.org/10.1080/09636412.2012.734234.
International Maritime Bureau Regional Piracy Center (IMB). (1992). IMB Annual Piracy Report. Kuala Lumpur: International Maritime Bureau Regional Piracy Center.
Peters, Bryan C. (2020). Nigerian piracy: Articulating business models using crime script analysis. International Journal of Law, Crime and Justice, https://doi.org/10.1016/j.ijlcj.2020.100410.
Petrossian, Gohar A. & Pezzella, Frank S. (2018). IUU fishing and seafood fraud: Using crime script analysis to inform intervention. The ANNALS of the American Academy of Political and Social Science, 679(1): 121-139, https://doi.org/10.1177/0002716218784533.
Shane, J.M., Piza, E.L., & Mandala, M. 2015. Situational crime prevention and worldwide piracy: A cross-continent analysis. Crime Science, 4(21): 1–13, https://link.springer.com/article/10.1186/s40163-015-0032-7.
Shane, M., & Magnuson, S., 2016. Successful and unsuccessful pirate attacks worldwide: a situational approach. Justice Quarterly, 33(4): 682-707, https://www.tandfonline.com/doi/full/10.1080/07418825.2014.958187.
About the author

Bryan Peters recently completed an MSc in criminology at KU Leuven (Belgium). For his thesis research he systematically assessed the harms of Nigerian piracy. Prior to his studies in Belgium he spent over 15 years as a criminal investigator and administrator with a large law enforcement and corrections agency in New Orleans, Louisiana. He also holds an MA in political science (with a concentration in international relations) from the University of New Orleans and a BS in political science (also with a concentration in international relations) from Northeastern University in Boston, Massachusetts. He recently published an article in the International Journal of Law, Crime and Justice and has another, co-authored with Dr. Letizia Paoli (KU Leuven), currently in press with Acta Criminologica: African Journal of Criminology and Victimology, focusing on the harms of Nigerian piracy. His research interests include maritime piracy, ‘blue crimes,’ harm reduction and crime prevention.
For a PDF of the commentary, please click here
- Forsyth et al., “Waterborne crime: Examining contemporary piracy”, 669-670.
- Cornish, “The procedural analysis of offending and its relevance for situational prevention”.
- Ibid, 175.
- Only one other study could be found applying crime script analysis to another ‘blue crime’. Refer to Petrossian and Pezzella’s (2018) analysis of IUU fishing and seafood fraud.
- IMB, IMB Annual Piracy Report, 1992, 2.
- Hastings, “Understanding maritime piracy syndicate operations”, 690-692.
- The be included in the analysis, incidents had to meet one of the following criteria:
1) Perpetrated in Nigeria’s internal waterways, territorial seas and contiguous and exclusive economic zones; or 2) Attributed to Nigerian pirates in the wider GoG, including the high seas; or 3) Committed on the high seas in locations where Nigeria was the closest littoral state.
- Greenfield & Paoli, “A framework to assess the harms of crimes”, 866.
- Per Greenfield & Paoli (2013: 870),
“Accompanying” activities are those that occur along with or are facilitated by the primary criminal activity, “Enabled” activities, also facilitated by the primary criminal activity, typically occur further downstream in the crime commission process than accompanying ones.
- See note 8.


1 thought on “Using crime script analysis to better understand piracy manifestations”
Comments are closed.